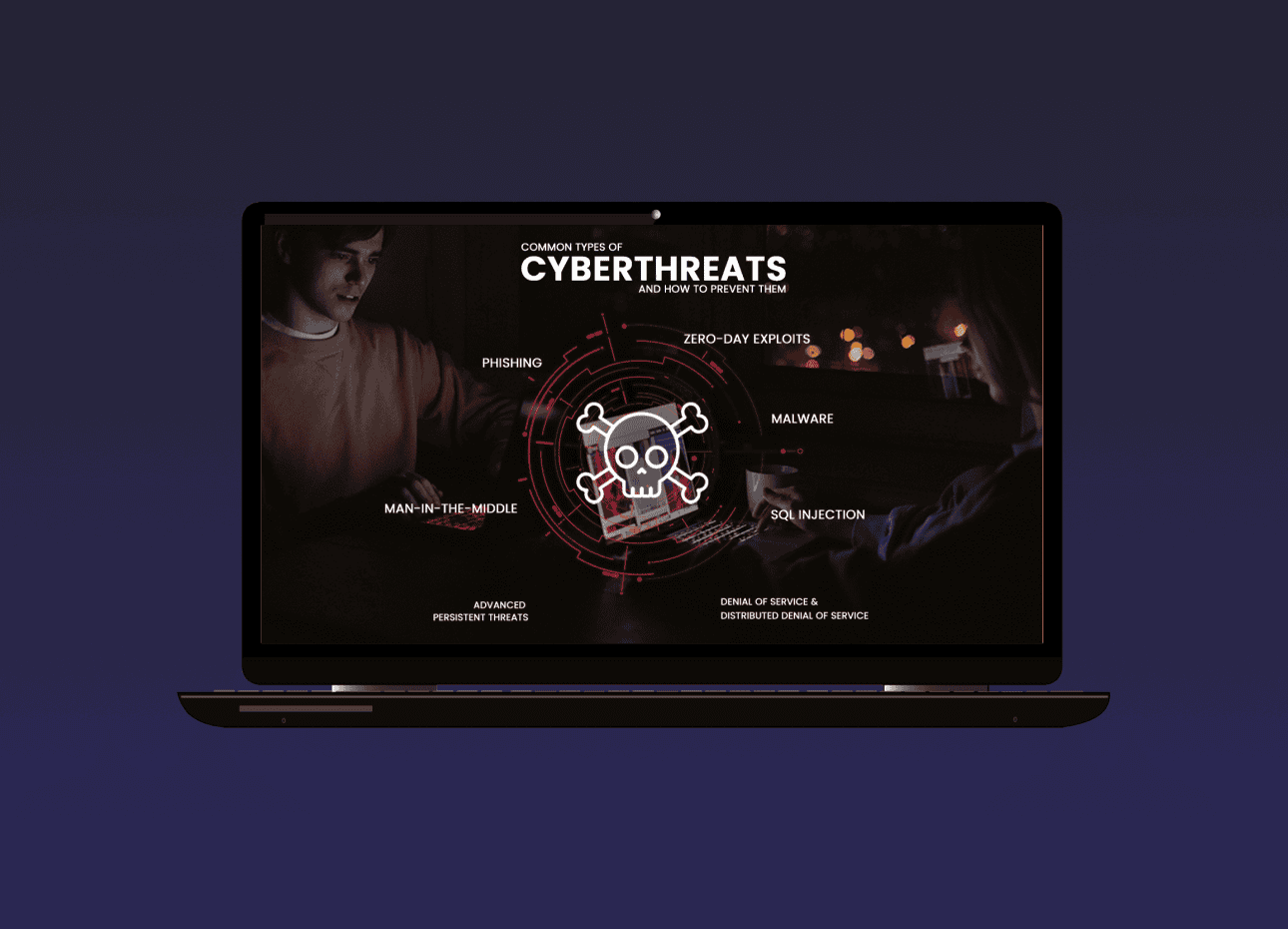
The Importance of Strong Passwords
Definition of Strong Passwords A strong password is a critical component of cybersecurity, designed to protect digital information from unauthorized access. It typically consists of a combination of uppercase and lowercase letters, numbers, and special characters, making it difficult to guess or crack. The complexity and uniqueness of strong passwords are what set them apart from weak, easily guessable ones. The Evolution of Password Security Password security has significantly evolved over the years. In the early days of computing, simple passwords sufficed to protect user accounts. However, with the advent of sophisticated hacking techniques and the proliferation of online services, the need for more robust security measures became evident. Today, strong passwords are a fundamental aspect of digital security protocols. Importance in the Digital Age In today’s digital age, where virtually every aspect of our lives is connected to the internet, the importance of strong passwords cannot be overstated. From…